[Deprecated] Single Sign-On (SSO) in TR/TM
NB: This page is now deprecated and should not be used for setting up new SSO integrations. SSO is no longer configured directly in TR and TM, but is now done in Talentech ID
Read more...
Terminology
Foreword
HRMTS offers an option to configure Single Sign-On (SSO) in the System. The SSO implementation is based on SAML 2.0, and is compatible with ADFS.
External Resources
Please see the following resources for more information:
HRMTS can be setup with 2 flows. The Service Provider Initiated (so called SP) implementation of SSO. It means that the end-users first navigate to the Service Provider (HRMTS) that initiates the authentication process by redirecting the user to the Identity Provider (Customer). The Identity provider initiated flow means that the users identify first with at their company's AD, and then click a link where they are redirected to HR Manager systems including the SAML token that is providing the login credentials.
Technical Flow
As described above, using the SP implementation, the users first navigate to the login page of the System. From here, the users are redirected to Customer's identity manager, with a signed SAML request, for authentication. Once on the Customer's side, the users are authenticated on Customer's network, and redirected back to the System with a signed SAML response. HRMTS decodes the SAML response, validates its contents, and finally grants the user access to the System.
Requirements
- The Customer must have the necessary infrastructure to support SSO.
- The users must also be configured in the System on before hand.
- Single Sign-On must be enabled for the Customer in System's configuration.
- Metadata must be exchange between System and Customer in order to configure SSO on both sides. The System metadata is not valid before the SSO setup with login/logout url is added, so first take Customer metadata and then add the System metadata at customers ADFS.
Required by HRMTS
The following information (metadata) is required to be configured in the System, and must be provided by the Customer.
- Customer's X509 certificate (Public Key) for signing the SAML request when redirecting users to Customer.
- Must be at least 256-bit encryption. (SHA-1 not accepted)
- The .cer file must be added to the file archive and referenced in the SSO setup.
- Customer's URL to redirect the users to for authentication.
- Customer's URL to redirect the users to when they log out of the System.
Required by Customer
Configuring AzureAd
If you are using AzureAD please set it up according to this description: [Deprecated] Azure AD (SAML) Setup for HRM SSO
The following information (metadata) is required to be configured on the Customer's side, and is provided by HRMTS.
- HRMTS' X509 certificate (Public Key) for signing the SAML response when redirecting users to back to System.
- System's URL to redirect the users to after authentication.
- Information about the claims to include in the SAML response.
- This information can be retrieved from the SAML metadata URL: https://recruiter.hr-manager.net/saml.aspx?customer=<ALIAS>, where <Alias> must be replaced with Customer's alias configured in the System.
Claims supported by us
To only do authentication the "mail" attribute is the only one that is required. This attribute must contain the email address that is used as username in HR Managers systems.
The customer can paste in this in claim rules in adfs:
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/department",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/tokenGroups"),
query = ";mail,givenName,sn,department,sAMAccountName,tokenGroups;{0}", param = c.Value);
Configuring ADFS
Active Directory Federation Services (ADFS) can pretty much configure itself automatically by supplying the above SAML metadata URL.
FAQ
Is the Identity Provider Initiated (IdP) option also available?
Yes. As the System basically accepts SAML Response from the Customer's identity manager as a stateless action, the System, implicitly, also support IdP.
Does HRMTS also support SAML/ADFS metadata file or URL?
Yes. If your implementation of SSO exposes a metadata URL, or produces a metadata file, it can be fed into the System for easier configuration. Simply, send it to HRMTS Support when you request to enable SSO.
Where do I find HRMTS' X509 certificate (Public Key) for signing the SAML response?
HRMTS' public key for SSO is embedded into the SAML metadata URL that is provided to the customer. E.g. https://recruiter.hr-manager.net/saml.aspx?customer=<ALIAS>, where <Alias> must be replaced with Customer's alias configured in the System.
Which unique name are users identified with in the System?
Users in the System are primarily identified with their unique email address. Even though the System supports storing users' unique id from the Customers' identity manager (e.g. sAMAccountName in AD), it is recommended to send email address as username in the SAML response.
Why do the users have to exist in the System before SSO can be used? Why can't the System just create them on-the-fly?
User provisioning (on-the-fly) during SSO is possible. However, it involves both more work to configure, as well as some practical challenges. It is therefore not recommended at all. If manual creation of users is a challenge for a Customer, it is recommended for them to use User Synchronization. Please see Which Integrations to Use? for more details.
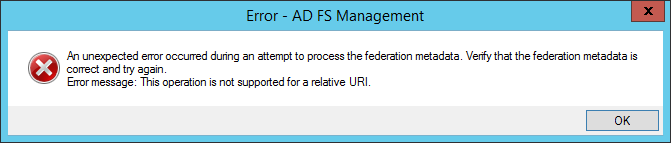
I am getting following error when configuring ADFS. What am I doing wrong?
You are getting this error, because you are using the metadata URL before SSO has been properly configured in the System. Please wait for the HRMTS Support to enable SSO for you first, then you can try again.
Can I set up different SSO settings for different departments?
No, SSO should be enabled and configured on root department only.
The saml signature could not be verified in the IdP flow
Check that the ADFS are sending the message signed. This is setup on the SamlResponseSignature property of the AdfsRelyingPartyTrust. It should include message, otherwise the verification of signature can be turned off on HR Manager's side.
Do you support 2-factor authentication?
When you set up single sign on via i.e. ADFS, the authentication and therefore also the responsibility for 2FA is moved from HR Manager to the customer. The customer will then need to configure 2FA in their own identity provider.
I get Invalid SAML response back from ADFS
The identity template https://recruiter.hr-manager.net/login.aspx?customer=xxx is not working properly and is cut to https://recruiter.hr-manager.net/login.aspx. This identifier must be changed to https://recruiter.hr-manager.net/xxx or just https://recruiter.hr-manager.net for customers that does not require more than one customer alias pointing to the same ADFS.